Red Hat CodeReady Dependency Analytics is a hosted service on OpenShift that provides vulnerability and compliance analysis for your applications, directly from your IDE. It automatically analyzes your software composition and provides recommendations to address security holes and licensing issues. The 0.1 release of CodeReady Dependency Analytics includes access to the Snyk Intel Vulnerability Database, which is a curated database of both unique and known open source software security advisories.
In this article, we’ll look at how the newest release of CodeReady Dependency Analytics improves your ability to detect, identify, and fix security vulnerabilities in your code through this integration.
The Snyk database
Snyk Intel is a fast, current, and complete vulnerability database used to proactively find and fix vulnerabilities and license violations in open source dependencies and container images. This database is continuously curated by an experienced team of security researchers and covers a wide range of vulnerabilities. Integrating CodeReady Dependency Analytics with Snyk helps developers increase their efficiency at containing open source security issues without losing their focus on development.
As shown in Figure 1, Snyk supports vulnerability reporting for most major programming languages and platforms.

Figure 1: Languages and platforms in the Snyk ecosystem.
Expanded vulnerability analysis in the IDE
Just as with previous releases, opening an application manifest file in your IDE automatically triggers dependency analysis. But in this release, the summarized vulnerability information shows separate counts for commonly known software vulnerabilities, as well as security advisories that are uniquely identified by Snyk. The IDE then shows the recommended software package version to fix the vulnerability. The demo in Figure 2 shows how to access vulnerability data and recommendations from the manifest file.
Improved stack analysis
With this release, we’ve also refreshed the CodeReady Dependency Analytics stack analysis report. When you launch a report, the Security Issues card now shows the number of vulnerable direct dependencies and the total count of vulnerabilities across them.
When you expand the Security Issues card, it presents separate tabs for public vulnerabilities that are commonly known and vulnerabilities that are uniquely identified by Snyk. Each tab shows a list of direct dependencies that have one or more vulnerabilities. Expanding the tab lets you see the details for each direct dependency. If a direct dependency has vulnerabilities due to its transitive dependencies, then you can drill down further into those details. The demo in Figure 3 shows how to access the range of information available in the new stack analysis report.
Viewing vulnerabilities
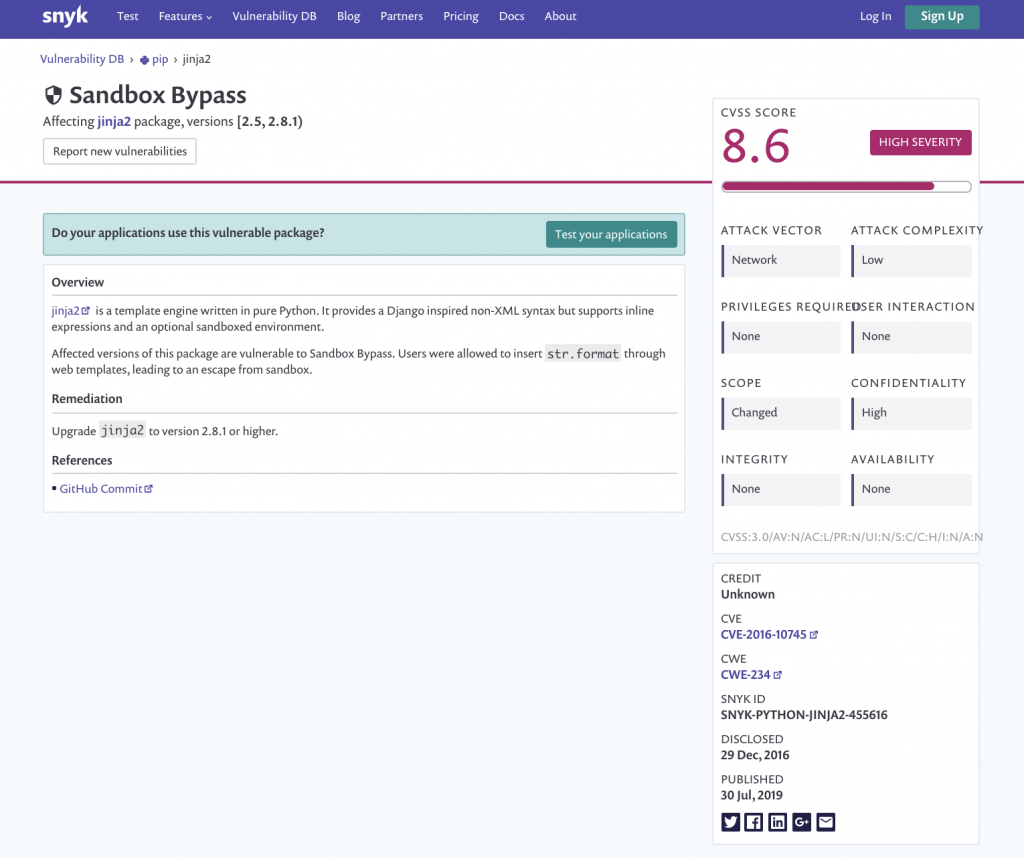
CodeReady Dependency Analytics now provides a clickable hyperlink for each commonly known vulnerability, which leads to the relevant Snyk vulnerability page. If you want to see additional details, such as known exploits for the vulnerability, you can register or sign-in to Snyk from this page. Figure 4 shows a common vulnerability page on the Snyk website.
Currently, you can access details about vulnerabilities unique to Snyk only from the Snyk website, which is shown in Figure 5.
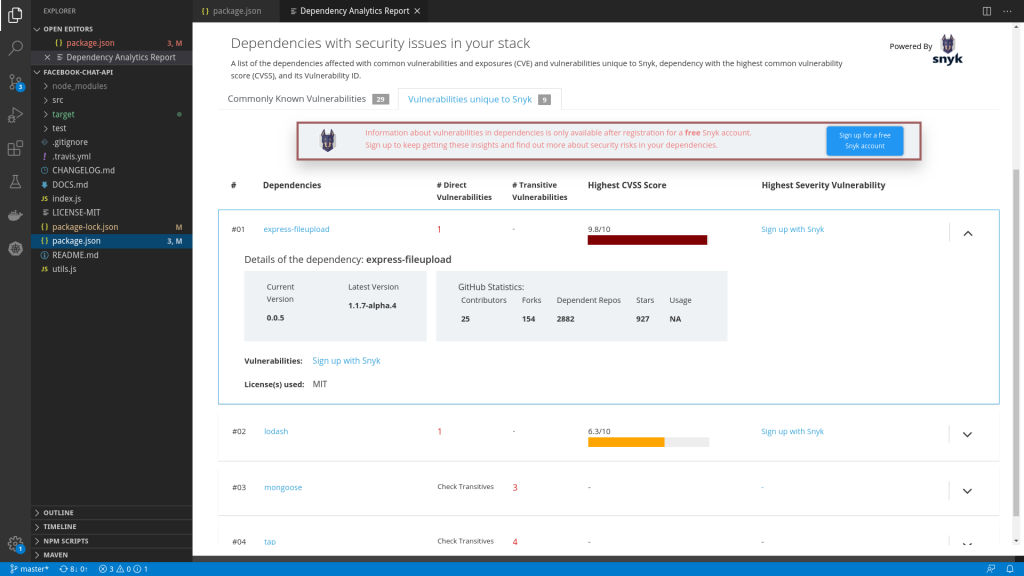
Figure 5: The stack analysis report lists dependencies and vulnerabilities unique to your application stack.
Advanced analysis and triage
Along with great vulnerability detection and fast identification, Snyk Open Source Security Management and Snyk Container also provide advanced capabilities for analysis and triage as shown in Figure 6. These tools let you make data-driven decisions and quickly fix security issues and reduce security exposure. As an example, you can use Snyk’s exploit maturity indicators to identify vulnerabilities that attackers could easily weaponize. This includes exploit maturity indicators to identify vulnerabilities that are easy for attackers to weaponize, and quick remediation with powerful fix advice.
In upcoming versions of CodeReady Dependency Analytics, developers registered with Snyk will have easier access to Snyk’s advanced analysis, including exploit maturity, vulnerable functions, existing patches, and malicious information about vulnerabilities.
Try CodeReady Dependency Analytics
CodeReady Dependency Analytics is available as an IDE plugin for Visual Studio Code (VS Code), Eclipse Che, Red Hat CodeReady Workspaces, and IntelliJ-based IDEs.
Follow these links to get the CodeReady Dependency Analytics IDE extension and provide your feedback.
- Get the VS Code extension for CodeReady Dependency Analytics.
- Get the IntelliJ IDE extension for CodeReady Dependency Analytics.
- Access CodeReady Dependency Analytics via the fabric8-analytics-server API.
- Provide your feedback on the Git issues repository.
We look forward to your feedback about this release of CodeReady Dependency Analytics. Stay tuned for further updates.
Note: The fabric8 Maven Plugin is now Eclipse JKube.
About Snyk
Snyk is a developer-first security company that helps software-driven businesses develop fast and stay secure. Snyk’s solution is built on Snyk Intel, a comprehensive, proprietary vulnerability database, maintained by an expert security research team. With tight integration into existing developer workflows, source control, and CI/CD pipelines, Snyk enables efficient security workflows and reduces mean-time-to-fix. For more information or to get started with Snyk for free today, visit https://snyk.io.
The post Vulnerability analysis with Red Hat CodeReady Dependency Analytics and Snyk Intel appeared first on Red Hat Developer.
from Planet Python
via read more
No comments:
Post a Comment